COSC1301 Introduction to Computing

Overview
Description:
Overview of computer systems—hardware, operating systems, the Internet, and application software including word processing, spreadsheets, presentation graphics, and databases. Current topics such as the effect of computers on society, and the history and use of computers in business, educational, and other interdisciplinary settings are also studied. This course is not intended to count toward a student's major field of study in business or computer science.
Learning Outcomes:
Upon successful completion of this Introduction to Computing course, you will be able to:
- Describe the fundamentals of computing infrastructure components: hardware, application software, operating systems, and data communications systems.
- Delineate and discuss societal issues related to computing, including the guiding principles of professional and ethical behavior.
- Demonstrate the ability to create and use documents, spreadsheets, presentations and databases in order to communicate and store information as well as to support problem solving.
- Describe the need and ways to maintain security in a computing environment.
- Explain how networks work; implement a basic home network.
- Describe basic concepts/structures of computer programming, demonstrate an understanding of programming strategies and design an algorithm.
Introduction
Welcome! During this course, you will be introduced to the world of computing. This includes: basic operating principles, security, capabilities, and limitations of computers and computer technology; using Internet resources to find and evaluate information and the basics of computer programming. You will also learn how to effectively use various tools to communicate via the Internet. These tools will include web pages, email clients, and other common computer applications as they become available. And finally, you will be immersed in the social factors associated with the use of computer technology. These factors include access issues, social issues, safety, credibility, and netiquette.
Module Overview
Module 1
This Module will help you understand how computers work and how to use them. We'll talk about how to set up a computer, the difference between hardware and software, and the types of computers you can use. We'll also explore operating systems, applications, the cloud, and much more.
Module Sections
1.1 What is a Computer?
1.2 Hardware Basics and Software Basics
1.3 Data Communications (The Internet, Networks, & IoT)
Module 2
This Module will help you understand ethics in the digital world and societal issues related to computing. You will learn about the impact of computers on society and the various computer careers available in the here and now. You will also explore the need and the implementation of information security, and much more.
Module Sections
2.1 Computer Ethics
2.2 Computers in Society
2.3 Computer Security
Module 3
This Module will teach you how to use common applications such as email, web browsers, word processing, and presentation software. You will learn how to create and format documents, spreadsheets, presentations, and databases. You will also explore the uses of these common applications to store information, support problem solving, and prepare professional reports.
NOTE: There is not much reading in this module as the best way to learn these topics is by doing. Run through the activities as many times as you feel necessary. The more you do, the more you will learn.
Module Sections
3.1 Common Computer Applications
3.2 Create, Format, Present
Module 4
This Module will help you understand how networks operate. You will learn about the hardware and software needed to operate a network, the varying types of networks and how information is sent in a network. You will also explore how to set-up a basic home network.
Module Sections
4.1 What is a Network?
4.2 Network Operations
4.3 Basic Home Networks
Module 5
This Module will help you understand what computer programming is and what the basic concepts/structures of computer programming are. You will gain a basic understanding of programming strategies and you will also explore designing an algorithm.
Module Sections
5.1 What is Computer Programming?
5.2 Programming Strategies/Algorithm Design
Module 1
Suggested Learning Activities
Discussion
Question: Are we (human beings) computers, in a sense? Why or why not?
Discuss your answer in detail. Engage at least two classmates. Do your best to defend your position with facts, not opinions!
Minimum requirements:
- Respond thoughtfully and respectfully to at least two classmates.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Cite any and all sources.
Question: What are the most important computer components/features for a small-business owner? A retired gentleman on a fixed income? A young college student?
Discuss your answer in detail. Engage at least two classmates. Do your best to defend your position with more facts than opinions!
Minimum requirements:
- Respond thoughtfully and respectfully to at least two classmates.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Cite any and all sources.
Question: Describe the functioning world if tomorrow the Internet were gone. What would it be like? What would be the most immediate challenges for society?
Discuss your answer in detail. Engage at least two classmates. Do your best to defend your position with facts, not opinions!
Minimum requirements:
- Respond thoughtfully and respectfully to at least two classmates.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Cite any and all sources.
Homework
SELL ME YOUR COMPUTER!
Research the model of your computer and create a sales document identifying/describing each of the following:
- Make and model of the computer.
- What type of personal computer it is.
- Methods of input and output (remember this does not mean ports).
- Type and amount of RAM and the maximum amount that the motherboard can accept.
- Number of expansion slots if any.
- Types of drives available to include their specifications.
Note! This is a sales pitch! Make me want to buy your computer!
Minimum requirements:
- A minimum of two full paragraphs. (DO NOT make a list or copy the specs from the Internet)
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Place a header on your page that contains your first and last name, the assignment name, and the course identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
Project
BUILD A COMPUTER!
Let’s challenge your understanding of computer hardware, software, and system requirements.
You are going to design a hypothetical computer for one of the three people described below. Your build will be a list of all the specifications that this system will have. In addition, you will need to write up a document explaining why you have selected these specifications, features, and components for the person you chose.
Requirements:
Choose to build a PC for one of the following.
- A retired gentleman on a fixed income
- A small-business owner
- A young college student
At a minimum you must consider the following items in your build.
- Cost
- Functionality
- Pre-installed applications
- Type of computer
- Motherboard
- Processor
- RAM
- Hard drive
- Power supply
- Video Card
- Peripherals
- Network access
- Operating system
- Any additional storage features or components
- Monitor
- Keyboard
- Mouse
- Speakers
Document minimum requirements:
- A minimum of three full paragraphs in addition to a neatly ordered spec list. (DO NOT copy the specs from the Internet)
- Submit only one document
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Include a cover page that contains your name, the assignment name, and the course identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
Assessment
IoT ECOSYSTEM
The goal of this project is to bring many of the strands together, in a grounded, real-world situation/scenario and which fully explores the potential and nature of connectedness.
The focus will be on ‘ecosystems’ of interacting internet appliances. You are going to consider how several different devices can work together to solve a shared problem.
What does an ‘ecosystem’ of IoT devices mean? Let’s use the analogy of cooking. To make a meal, we don’t just use one ‘thing’; we use a series of ‘things’ together. To cook our dinner, we need our fridge to store and keep the food fresh, a knife to chop, and cutting board to prepare on, a tin opener, a saucepan, an oven, etc. All of these things work together to help us achieve the overall goal. Each of them as a specific function within the overall task. The same is true of the Internet of Things; real-world problems are complex, and often require a series of complementary devices or interacting systems that work with one another to achieve the desired outcome.
- Do some research and then some brainstorming and develop a future IoT concept for a major industry of your choice. You are to imagine a scenario that could feasibly exist in 5 years’ time. This should include a vision for an ecosystem of interacting connected products. This ecosystem would solve a problem, enhance the experience of your selected industry (or any aspect of it), or just make day-to-day life activity easier.
- You will need to develop (in theory) two to three device ideas that illustrate this concept and that interact with one another to support your problem or experience from item one. You must explain what they do and how they work together with each other.
- Submit your proposal in well-formed sentences and paragraphs. Cite any sources used.
NOTE: Remember that this is an assessment, put some thought into this and be very thorough and extensive in your submission. A few sentences is not sufficient.
Minimum requirements:
- A minimum of four full paragraphs.
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Place a header on your page that contains your first and last name, the assignment name, and the course identifier
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
1.1 What is a computer?
According to Dictionary.com, a computer is “a programmable electronic device designed to accept data, perform prescribed mathematical and logical operations at high speed, and display the results of these operations.”
Watch the video to get an idea of what a computer really is. Think about this question: Are we (human beings) computers?
Direct video URL: https://www.youtube.com/watch?v=mCq8-xTH7jA Video length: 5:09
A computer has four basic functions, these are input, process, output, and storage. Referring back to the question above, human beings perform the four basic functions and therefore could possibly be categorized as a computer.
- We have input in the form of our five senses.
- Our brain has a memory component which stores important information and discards unnecessary items.
- Our brain processes thoughts and ideas based on what is received from the five senses.
- We send output via speech, body language, and facial expressions.
Honestly, why do we even need computers?
1.2 Hardware and Software Basics
There are two major components of a computer system. These are hardware and software. The hardware is the physical components both inside the computer and outside the computer that mechanically operate the computer. The software is not a physical item but is still very real and assists the hardware by providing instructions and commands to also assist in operations
Hardware Basics
Computer hardware consists of the physical components of a computer system. It includes components inside the computer and outside the computer. The box containing the internal components of a basic desktop computer has many names such as chassis, tower, case, or system unit. This is the main external component of the computer which houses all the internal components. Internal components inside the case include the central processing unit (CPU), the motherboard, and two different types of memory storage, the power supply, and various expansion slots. Hardware components that are not necessarily required for the computer CPU to operate are usually called peripherals which can include secondary storage and input and output devices.
Hardware External Components
Secondary storage can technically be an external or an internal hardware component of a computer. There are a few different types of external secondary storage such as external hard drives and flash drives. This type of storage is usually portable and allows a person to carry data with them to use in other computers as needed.
The list of input and output hardware components seems unending. An input device is used to provide data or instruction to a computer. If a device is used to make the computer perform an action then it is considered an input device. A keyboard and a mouse or touchpad were probably the most common forms of input until touchscreens became popular. Keyboards, mice, and touchpads are still used of course, but only with stationary systems. Most mobile devices such as phones and tablets are now touchscreen. What are some other devices that are a computer input component?
Output devices provide the results of the action that your input devices request. The most common output devices are the monitor or screen and printers. For example, you could use the keyboard to type or input the math problem 5+6 into an on-screen calculator and the result of 11 displayed on the screen is the output. You can also go further and send a command to the printer to print the result for an additional form of output. What are some other devices that are computer output devices?
Hardware Internal Components
The motherboard is the main internal hardware component which connects all the other components together. The CPU resides on the motherboard and all circuits on the motherboard can be traced in some path back to the CPU. The CPU is the brain of the computer and all commands are processed here which are directly obtained from information residing in storage. The computer has internal storage in two categories, primary and secondary. Recall the mention that secondary storage could be considered both internal and external. Internal secondary storage is the computer’s internal hard drive and can also be a CD or DVD drive built in to the computer case. The primary storage is the random-access memory (RAM) and is commonly just called the computer’s memory. The RAM is the primary storage because it stores the information that is directly accessible by the CPU. The CPU fetches commands from the RAM and processes them in a sequential order. Oftentimes these commands require action from other internal components further down the line. Many of these components are in the form of cards which are contained in expansion slots on the motherboard. These can include video cards, sound cards, network cards, and so on. For example, many people who use their computers for online-gaming require increased video graphics and audio capabilities to make their gaming experience the best possible. Their computers will have higher capability video and sound cards inserted into the motherboard expansion slots to facilitate this optimal experience. Of course, none of these internal components can operate without a power source which is known as the power supply. Maybe the power supply is the most important internal component of all?
Software Basics
For hardware components to interact and perform, they require some sort of software. Software is an intangible component meant to activate and control the hardware and process input and output commands. There are two main types of software; system software and application software. Application software makes life easier for the end-user of a computer by allowing them to perform specific tasks such as sending an email or typing a letter. Examples of application software include word processing and graphics design software. System software supports internal computer function, manages hardware resources and provides a platform for application software to run upon. Some examples of system software include operating systems, device drivers, and system utilities. The operating system is of great importance and controls how signals move inside the box. In the next section we will cover how data moves between separate boxes or computers: data communications.
Watch the video below to get an overview of hardware and software.
Direct video URL: https://www.youtube.com/watch?v=xnyFYiK2rSY Video length: 5:22
1.3 Data Communications
According to Dictionary.com, data communications is the electronic transmission of information that has been encoded for storage and processing by computers. The systems that carry the electronic transmission of information are called networks. The largest and most well-known network is the Internet.
Watch the videos below for a better understanding of the Internet and the data communications of today.
What is the Internet?
Direct video URL: https://www.youtube.com/watch?v=Dxcc6ycZ73M Video length: 3:44
The Internet; Wires, Cables, and WiFi
Direct video URL: https://www.youtube.com/watch?v=ZhEf7e4kopM Video length: 6:41
Cloud Computing Explained
Direct video URL: https://www.youtube.com/watch?v=QJncFirhjPg Video length: 1:06
Internet of Things Explained
Direct video URL: https://www.youtube.com/watch?v=5d1bZ2MBdvI Video length: 2:26
Internet of Things – TEDx Talk
Direct Video URL: https://www.youtube.com/watch?v=_AlcRoqS65E Video length: 16:37
Computer Basics
Complete the tutorials found at the link below to better understand computer basics.
https://edu.gcfglobal.org/en/computerbasics/
These tutorials are provided by Goodwill Community Foundations and cover the following topics.
- Getting to Know Computers
- Understanding Operating Systems
- Understanding Applications
- Web Apps and the Cloud
- Basic Parts of a Desktop Computer
- Buttons, Sockets and Slots on a Desktop Computer
- Inside a Desktop Computer
- Laptop Computers and Netbooks
- Getting to Know Mobile Devices
- Setting Up a Computer
- Beginning to Use Your Computer
- Getting to Know the OSv
- Connecting to the Internet
- Computer Safety and Maintenance
- Basic Troubleshooting Techniques
Work through the Computer Basics Lessons, Interactives, and take the quiz under Extras. The quiz is not graded, but will provide you a good feedback on your understanding of the content.
Computer Components
Complete the tutorials found at the link below to better understand the components of computers.
https://www.javatpoint.com/computer-components
These tutorials are provided by JavaTpoint and cover the following.
- Computer Components
- Input Devices
- Output Devices
- Central Processing Unit
- Hardware
- Software
Internet of Things (IoT) and IoT Devices
Complete the tutorials found at the link below to better understand the concepts of IoT.
https://www.javatpoint.com/iot-tutorial
These tutorials are provided by JavaTpoint and cover the following.
Internet if Things (IoT)
- IoT Tutorial
- Advantage & Disadvantage
- Embedded Devices and System
- IoT Ecosystem
- IoT Decision Framework
IoT Devices
- Smarts Objects
- IoT Devices
Module 2
Suggested Learning Activities
Discussion
Question: Of the entities and their ethics guidelines that you reviewed in section 2.1, which were the most thorough and why? Which ones did you find lacking? What do you feel they were missing?
Discuss your answer in detail. Engage at least two classmates. Do your best to defend your position with more facts than opinions!
Minimum requirements:
- Respond thoughtfully and respectfully to at least two classmates.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Cite any and all sources.
Question: What do you believe is the worst affect that technology has had on society?
Discuss your answer in detail. Engage at least two classmates. Do your best to defend your position with more facts than opinions!
Minimum requirements:
- Respond thoughtfully and respectfully to at least two classmates.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Cite any and all sources.
Question: National Cybersecurity defense. Do you believe it is acceptable for the U.S. to spy and attempt to hack into the computer systems of other countries? Why or Why not? What about those countries reciprocating? Is that acceptable? Why or why not?
Discuss your answer in detail. Engage at least two classmates. Do your best to defend your position with more facts than opinions!
Minimum requirements:
- Respond thoughtfully and respectfully to at least two classmates.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Cite any and all sources.
Homework
Select three of the scenarios below and write up a paragraph for EACH scenario analyzing the ethical issues. Use the Ten Commandments of Computer Ethics as your frame of reference. At a minimum, identify the violator(s), violation(s), which commandment(s) they violate, why, and/or how, and what you feel should happen to the violator(s).
- A company’s employee uses their work computer to test some software that their friend bought. It only takes a few minutes and they uninstall it after they are done.
- A company’s employee gives a friend who works at a different company a copy of a proprietary software for them to use.
- A company’s employee was curious as to what the “higher-ups” pay looks like.They break the passcodes and take a quick peek at the salaries.
- A bank teller transfers money from a customer account into their account to pay a bill that is overdue. Three days later, the bank teller gets paid and transfers the money back.
- A college student shares their password and computer lab access id with a fellow student who is not taking a computer class that requires a lab. The fellow student uses three hours of computer time to complete the government homework and prints a few recipes for their mom.
- You are a software developer and you are asked to develop an app that will intentionally generate inaccurate information for a client. You are told in no uncertain terms that you must develop the app or lose your job. You write the program.
Be sure to reference ethical guidelines you learned from the module content and clearly identify the ethical dilemma(s) and/or violation(s).
Minimum requirements:
- A minimum of one full paragraphs per each scenario
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Place a header on your page that contains your first and last name, the assignment name, and the course identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
Project
Consider the various categories of ethics from the module content;
- Internet Ethics
- Cyber Ethics
- E-Commerce Ethics
- Web Ethics
- Business Computer Ethics
- Consumer Computer Ethics.
For this assignment, you will select three of the categories above and write up a detailed scenario for each selection where an ethical dilemma occurs related to the respective category. Include in each write-up, a description of how the dilemma could have been prevented or avoided and what actions should be taken to reprimand or punish any participants. Be sure to reference ethical guidelines you learned from the module content and clearly identify the ethical dilemma(s) and/or violation(s).
Minimum requirements:
- A minimum of two full paragraphs per each scenario
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Include a cover page that contains your name, the assignment name, the course identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
Assessment
IoT Through the Lens of Ethics and Security
The goal of this project is to improve on your IoT concept using your new knowledge. Reflect on your Module 1 Independent Project and your IoT design and plan. Now that you have a frame of reference for the concepts of computers in society, computer ethics, and computer security, you will need to apply that frame to your IoT design and plan.
- Consider your IoT concept and devices and run every aspect of it through each of the ten commandments of computer ethics. Are there violations, existing or potential? How can you fix or prevent the violations? Write your findings out in well-formed paragraphs.
- Now apply what you have learned regarding computer security to your IoT concept and devices. What are the potential risks? How can they be mitigated or avoided altogether? Write your findings out in well-formed paragraphs.
- Submit your responses to items one and two in well-formed sentences and paragraphs. Be sure to cite sources used.
NOTE: Remember that this is an assessment, put some thought into this and be very thorough and extensive in your submission. A few sentences is not sufficient.
Minimum requirements:
- A minimum of three full paragraphs.
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Place a header on your page that contains your first and last name, the assignment name, and the course identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
NOTE: Remember that this is an assessment, put some thought into this and be very thorough and extensive in your submission. Minimalistic work is not sufficient and will be graded accordingly.
2.1 Computer Ethics
According to Dictionary.com, ethics is “a system of moral principles” which leads us to the understanding that computer ethics would be the system of moral principles regarding all aspects of computing.
The Ten Commandments of Computer Ethics by the Computer Ethics Institute
- Thou shalt not use a computer to harm other people.
- Thou shalt not interfere with other people's computer work.
- Thou shalt not snoop around in other people's computer files.
- Thou shalt not use a computer to steal.
- Thou shalt not use a computer to bear false witness.
- Thou shalt not copy or use proprietary software for which you have not paid.
- Thou shalt not use other people's computer resources without authorization or proper compensation.
- Thou shalt not appropriate other people's intellectual output.
- Thou shalt think about the social consequences of the program you are writing or the system you are designing.
- Thou shalt always use a computer in ways that ensure consideration and respect for your fellow humans.
There really is no universal standard set by one entity regarding computer ethics. There are several professional societies that have created some basic computer ethics guidelines.
Research and review the following entities and their specific computer ethics guidelines. Pay special attention to any similarities and/or differences between them.
Association for Computing Machinery (ACM)
ACM Code of Ethics and Professional Conduct
Australian Computer Society (ACS)
ACS Code of Ethics
ACS Code of Professional Conduct
British Computer Society (BCS)
BCS Code of Conduct
Code of Good Practice
Institute of Electrical and Electronics Engineers (IEEE)
IEEE Code of Ethics
IEEE Code of Conduct
Information Technology Alliance (ITA)
Code of Professional Conduct
League of Professional System Administrators (LOPSA)
The System Administrators' Code of Ethics
Under the umbrella of computer ethics, a person could easily parse out subcategories such as Internet Ethics, Cyber Ethics, E-Commerce Ethics, Web Ethics, Business Computer Ethics, and Consumer Computer Ethics. Consider each subcategory and devise an ethical scenario that fits each one of the categories. Write these down! You will need them later!
Watch the video to view more. Think about this question: Can a computer be ethical or is only the end-user responsible for the practice of ethics?
Digital ethics and the future of humans in a connected world
Direct video URL: https://youtu.be/bZn0IfOb61U Video length: 19:52
2.2 Computers in Society
Computers have inarguably made our lives easier yet there have been a few drawbacks as well. Think about things like privacy, communication, fraud, bullying, addiction, health, and employment opportunities before and after computers. How has the mass implementation of technology affected these topics? Are there solutions to these issues?
Review the videos and article links below while considering these questions.
Direct video URL: https://youtu.be/tvbU00dpnlg Video length: 14:58
What Are the Benefits of Computers in Society?
https://tinyurl.com/yy4fvzby
Disadvantages of Computers in Society
https://tinyurl.com/y3z8tmzf
The Impact of Computers on Employment
https://tinyurl.com/y5j989n8
15 of the most promising jobs in the US in 2019, according to LinkedIn
https://tinyurl.com/yadkdrht
The 25 most in-demand technical skills of 2019, according to LinkedIn
https://tinyurl.com/yypx2zle
2.3 Computer Security
According to Dictionary.com, security is defined as the precautions taken to guard against crime, attack, sabotage, espionage, etc. Therefore, computer security would be the precautions taken to guard computers and our digital environments. The current buzzword for computer security is cybersecurity and before that it was information security, but sometimes terms are not appropriately interchangeable.
Let’s begin with information security. According to the SANS institute (SysAdmin, Audit, Network and Security), information security refers to the processes and methodologies which are designed and implemented to protect print, electronic, or any other form of confidential, private and sensitive information or data from unauthorized access, use, misuse, disclosure, destruction, modification, or disruption. In the simplest terms, this means that a locked door to a file room with both paper and electronic files is considered information security.
Cybersecurity is a more defined subset of information security. According to National Institute of Standards and Technology (NIST), a unit of the U.S. Commerce Department, cybersecurity is the prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation (the assurance that a sender cannot deny authenticity). Nowadays we have separate focus on different types of information and a much stronger focus on electronic information.
Check out this article for a more in-depth explanation the watch the videos below for a better understanding of these concepts:
Cybersecurity vs. Network Security vs. Information Security https://tinyurl.com/ya4n3atg
Direct video URL: https://www.youtube.com/watch?v=d30n-YxOHo4 Video length: 22:17
Direct video URL: https://www.youtube.com/watch?v=ooJSgsB5fIE Video length: 19:08
Cybersecurity
For in-depth coverage of Cybersecurity, complete the tutorial below.
https://www.javatpoint.com/cyber-security-tutorial
These tutorials are provided by JavaTpoint and cover the following topics.
- What is Cyber Security
- Cyber Security History
- Cyber Security Goals
- Types of Cyber Attacks
- Types of Cyber Attackers
- Cyber Security Principles
- Data Security Considerations
- Cyber Security Technology
- Threats to E-Commerce
- Cyber Security Policies
- Cyber Security Standards
- Digital Signature
- Cyber Security Tools
- Cyber Security Challenges
- Security Risk Analysis
To navigate through the tutorial, click the green “next” button located both at the top and at the bottom of each page.
Module 3
Suggested Learning Activities
Discussion
Question: What are the top three computer applications that you use? Why or for what do you use them? Tell the class what the pros and cons are of those specific applications.
Discuss your answer in detail. Engage at least two classmates. Do your best to defend your position with more facts than opinions!
Minimum requirements:
- Respond thoughtfully and respectfully to at least two classmates.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Cite any and all sources.
Homework
Email Editing, Mark-up, and Review
Fix the emails! We have covered some email etiquette in the module now let's see what you have learned.
Using Microsoft Word and the included Review and Markup tools, copy and paste the six poorly written emails below, and then correct them. Be sure to utilize the options in MS Word to show all mark up and track changes and show all comments so that I can see all of your edits!
Minimum requirements:
- Submit only one document.
- Use the review tools in MS Word as indicated
- Place a header on your page that contains your first and last name, the assignment name, and the course identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
-------------------------------------------------------------------------------------------------
To: Bobby Hogue From: John Moore Subject: Job? Hey Bob, We talked a couple weeks back at the chamber of commerce event. (I was the one looking for a summer internship and had a zit on my lip that could have passed for a cold soar. Lol. Whew. It was not. You’re probably like, “uh.. What?” Maybe that helps you recall, maybe not. Not completely important, I suppose. I’d really like to come work for you atyour IT business. You seemed like a cool person to work for, I liked ur striped pants. I’m available to start working on Monday, but I am taking my driver’s test in June and have to study and go an hour and half away to take it at an easier place cause I’m not a great driver so I’ll miss a few days. I am also going to the beach with friends for a week in July. Oh, and my grandmother has bad gas (OMG IT’S TERRIBLE) and sometimes I have to take her to the doctor. I’ve attached my resume, it’s the bomb dot com. Let me know if you have a job opening for me. I can’t wait to play on some computers. If I don’t respond to your email, I’m always on FB, snapchat or insta! Peace out, Ginny Moore --------------------------------------- From: Heather D CC: Every single human Heather has ever emailed Subject: Fwd: Fwd: Fwd: Fwd: OMG funny pictures of hilariousness OMG this is the best email I’ve seen all day. Hope you it. -Delight ----------------------------------------- From: Karen Grode To: Anastasia Simoncini Subject: ... Did you see what Bratney is wearing today? She looks stupid. I mean, that color lipstick? She’s probably trying to get Bryan’s attention. And did you hear her sucking up to the boss. I can’t stand it. Like, we all work hard. AM I RIGHT? -------------------------------------- From: Christina Tintle To: Caroline Sherp Subject: Today’s Meeting Hey beautiful! I am looking forward to seeing you today for our meeting. I’ve attached the materials needed for our discussion. Let me know if you have any questions. Regards, Christina Tintle Marketer Extraordinaire hotpartychick@ Christinasmarketing.com (555) 545-5656 “Be so good they can’t ignore you.” –Steve Martin ------------------------------------ To: Employer From: Ty Keister Subject: I need jobz der Employer, I wud like 2 apply 4 da job in customer service. I saw ur job on FB. I got my resume and added it to da email. I wudappreci8 ur response. -TK
------------------------------- To: Jimmy Slocum From: Adam Sandler Subject: Presentation Dear Mr. Sandler: Can you send me the presentation from last week? I really enjoyed it! Sincerely, Jimbo
Project
There are already standards in place for commercial emails, should there be specific email standards for other email communication? At the bare minimum what should be required and why? Who would enforce the policies? What types of emails would it apply to?
Create a proposal of a national or international set of standards for electronic communications. You can address only email or you can try to expand your standards to encompass other communication such as instant messaging and text messaging in addition to email. You must clearly categorize and identify the types of electronics communications to which your standards will apply and identify what entity in the computing world should "own" the policing and updating of these standards.
Minimum requirements:
- A minimum of three pages in the document not including cover page and citations page.
- Arial or Times New Roman font no larger than 12 point
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Include a cover page that contains your name, the assignment name, and the course identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
Assessment
The goal of this project is to demonstrate your ability to use common applications to communicate and store information. You will use your IoT design and plan for this assignment. Now that you have learned how to use email, web browsers, and productivity software, you can start to apply those skills.
- First, you will use Microsoft Word to create a professional proposal document that is intended for some potential investors of your idea. It will need to be a comprehensive report using various formatting and styles. It should have clearly defined sections, images, and supporting tables and charts with data (fictional but realistic) regarding cost and other considerations. Apply as many of the concepts you learned in the tutorials as are reasonable to make this proposal look and feel professional.
- Next, you will use Microsoft Excel to continue the proposal by created spreadsheets with formulas and formatting to enhance the proposal. Whatever data you wish to invent and provide, there must be actual formulas used to calculate in the spreadsheet. You must also have both absolute and relative cell references, and at least one function. You will need to be sure to reference the spreadsheet in your proposal as an attachment or appendix. Remember this is part of a professional package that is intended for your investors! Make it look polished!
- Then, you will create a Microsoft PowerPoint presentation that gives a solid overview of your proposal and spreadsheets. There should be charts and tables derived from your Excel spreadsheet data, as well as information and images relating to your Word document inserted into the presentation. You must also apply themes, animations, and transitions to your work.
- Once your three artifacts are complete, reviewed, and polished, you will create a folder in your OneDrive to store these items and upload them there.
- Create a shared link to this folder.
- Draft an "email to your investors" (me). In a professional, business-like tone, you will ask them to review your documents via the link and consider your proposal in so many words. DO NOT COPY the previous sentence and assume that is enough for the body of the email. Your email must contain the link to your files!
- Submit the email with link.
NOTE: Remember that this is an assessment, put some thought into this and be very thorough and extensive in your submission. Minimalistic work is not sufficient and will be graded accordingly.
3.1 Common Computer Applications
Think back to some of the tutorials in Module 1. You learned about application software which is a type of software that performs specific tasks. Some of the most common applications in use today include word processors, web browsers, email, media players, and real-time communication applications. There are also spreadsheet, presentation, and database applications which are more common in the business world and when combined with word processor applications, they are called productivity software. We will go more in depth into email, web browsers and productivity software in the next section.
Review the articles at the links to get a better understanding of computer applications and why proficiency with them is important.
The best web browser 2019
https://www.techradar.com/news/the-best-web-browser
The 8 Best Email Clients for Windows in 2019
https://tinyurl.com/y5p9vqhx
Office 365 vs G Suite
https://tinyurl.com/y9svoveo
Computer Skills: Definitions and Examples
https://tinyurl.com/y2q2l8sq
3.2 Create, Format, Present
Probably the most used and most important applications for any person or business are email, web browsers, and productivity software. After all, how else would we navigate the Internet and conduct business in the virtual world?
Complete the tutorials found at the link below to better understand the capabilities of email applications.
https://edu.gcfglobal.org/en/email101/
These tutorials are provided by Goodwill Community Foundations and cover the following topics.
- Introduction to Email
- Common Email Features
- Contacts and Calendars
- Email Etiquette and Safety
- Time-Saving Email Tips
- Email Violations Can Jeopardize Your Job
- Avoiding Spam and Phishing print
- How Formal Should an Email Be?
Work through the Email Basics Lessons, Interactives, and take the quiz under Extras. The quiz is not graded, but will provide you a good feedback on your understanding of the content.
Web Browsers and the Internet
Complete the tutorials found at the link below to better understand the capabilities of web browsers and navigating the Internet.
https://edu.gcfglobal.org/en/internetbasics/
These tutorials are provided by Goodwill Community Foundations and cover the following topics.
- What is the Internet?
- What Can You Do Online?
- Getting Started with the Internet
- Connecting to the Internet
- Understanding the Cloud
- Using a Web Browser
- Understanding Hyperlinks
- Downloading and Uploading
- Using Search Engines
- Understanding URLs
- How to Set Up a Wi-Fi Network
- Choosing a Web Browser
Work through the Internet Basics Lessons, Interactives, and take the quiz under Extras. The quiz is not graded, but will provide you a good feedback on your understanding of the content.
Productivity Software (Microsoft Office Suite)
What is a business without productivity? There are several productivity suites available, but Microsoft Office is certainly one of the most recognized.
NOTE: Before you begin these lessons, you will need to ensure that you have access to the most recent version of Microsoft Office.
Complete the tutorials found at the link below to better understand the capabilities of web browsers and navigating the Internet.
MS Word
MS Excel
- https://edu.gcfglobal.org/en/excel/
- https://edu.gcfglobal.org/en/excelformulas/
- https://edu.gcfglobal.org/en/excel-tips/
MS PowerPoint
MS Access
https://edu.gcfglobal.org/en/access/
These tutorials are provided by Goodwill Community Foundations
Work through the Word, Excel, PowerPoint, and Access Lessons, Interactives, and take the quiz for each under Extras. The quiz is not graded, but will provide you a good feedback on your understanding of the content.
Module 4
Suggested Learning Activities
Discussion
Question: Research and describe at least three different kinds of computer networks. What are the advantages and disadvantages for each?
Discuss your answer in detail. Engage at least two classmates. Do your best to defend your position with more facts than opinions!
Minimum requirements:
- Respond thoughtfully and respectfully to at least two classmates.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Cite any and all sources.
Homework
Consider the network analogy from the module content (included below). Review how the data flow in the analogy correlates to the TCPIP model. Identify and thoroughly discuss three issues that you could foresee occurring in the flow. Also, include your thoughts on how or if it can be prevented or mitigated.
Minimum requirements:
- A minimum of three full paragraphs.
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Place a header on your page that contains your first and last name, the assignment name, and the course identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
Module 4 Network Analogy
You write a letter to your friend in Central City, Ohio, put their physical address on the envelope, and place it in a United States Postal Service (USPS) drop box for routing and delivery. A mail carrier retrieves your letter and all the other mail from the drop box and takes it to a local location (post office) for sorting and routing. At the post office, your letter and other items are sorted according to the state listed on the envelope. All mail including your letter that is going to Ohio is loaded onto a truck or plane and transported to a new sorting location in Ohio. At that location, the mail is sorted by cities in Ohio, your letter gets put in the Central City pile and is again shipped off, most likely by truck to a location in Central City. At this location, the mail is all sorted according to the zip code first and then the actual street address, placed with a mail carrier and sent out for delivery. Your friend receives your letter and the process is complete. This is the basic idea of how a network transmits electronic information.
Project
In this assignment, you will write up your own network analogy. The analogy in the lesson used snail mail (included below for your review) so you will make your own using some other concept. For example, you could go big as a country or go smaller and use a school, office, your home, or something else. The more creative the better but it must be clear that you understand the flow of information. Make sure to reference the TCP/IP model and use other terms that you learned in this module. Additional independent research is strongly encouraged for any terms or concepts that you are not completely clear on.
- Review the module sections, do some research and then some brainstorming and develop a network analogy like the one in the module and shown below.
- You will need to demonstrate that you understand the terminology and the flow of the information and how each stage of information flow works. You must explain in some detail what is occurring at each ‘stop’, how, and why when possible.
- Submit your analogy in well-formed sentences and paragraphs.
Minimum requirements:
- A minimum of two full paragraphs.
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Include a cover page that contains your first and last name, the assignment name, and the course identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
Module 4 Network Analogy
You write a letter to your friend in Central City, Ohio, put their physical address on the envelope, and place it in a United States Postal Service (USPS) drop box for routing and delivery. A mail carrier retrieves your letter and all the other mail from the drop box and takes it to a local location (post office) for sorting and routing. At the post office, your letter and other items are sorted according to the state listed on the envelope. All mail including your letter that is going to Ohio is loaded onto a truck or plane and transported to a new sorting location in Ohio. At that location, the mail is sorted by cities in Ohio, your letter gets put in the Central City pile and is again shipped off, most likely by truck to a location in Central City. At this location, the mail is all sorted according to the zip code first and then the actual street address, placed with a mail carrier and sent out for delivery. Your friend receives your letter and the process is complete. This is the basic idea of how a network transmits electronic information.
Assessment
Let’s challenge your understanding of computer network requirements.
You are going to design a hypothetical network for one of the three people described below. Your design will be a list of all the specifications that this network will have. In addition, you will need to write up a document explaining why you have selected these specifications, features, and components for the person you chose.
Choose to design a network for one of the following.
- A retired gentleman on a fixed income
- A small-business owner
- A young college student
At a minimum you must consider the following items in your design.
- Cost
- Functionality
- Connecting devices
- Internet connections
Devices to consider on your network can include but are not limited to:
- Printers
- DVRs
- Smart TVs
- Gaming Consoles
- Appliances
- Computers
- Mobile devices
- Digital media players
- Smart home devices
Document minimum requirements:
- A minimum of three full paragraphs in addition to a neatly ordered equipment list. (DO NOT copy the list from the Internet)
- Your submission must have five to ten devices excluding the modem and router.
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Include a cover page that contains your first and last name, the assignment name, and the course code identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
NOTE: Remember that this is an assessment, put some thought into this and be very thorough and extensive in your submission. Minimalistic work is not sufficient and will be graded accordingly.
4.1 What is a network?
In a previous module, we discussed data communications. We learned that data communication is the electronic transmission of information and that the systems that carry the electronic transmission of information are called networks. Networks make our digital activities possible in current times. Especially the largest and most well-known network; the Internet.
Recall the video, What is the Internet? from Module 1. The Internet was described as a fully distributed system with no central control, consisting of many independently operated networks. So, let’s scale down the infrastructure of the Internet to get a solid view of what really is a network.
If we look up the definition of the word network, we get; “an arrangement of intersecting horizontal and vertical lines” or “a group or system of interconnected people or things.” When we factor in that electronic information is being transmitted, we have a computer network. A network can be as small as two devices communicating such as the small graphic below or as large as the Internet as we have already learned.
In the abstract sense, these two computers are connected.

4.2 Network Operations
One of the hardest things to grasp, however, is what the network would look like. Envisioning electronic data flow isn’t really a concrete thought. Let’s look at an analogy that is more grounded.
When you send a letter in the mail, you are sending it via a network, albeit a more physical version! Have you ever really thought about what path that letter traveled to get to its destination? The following scenario for a better idea of how this process works.
You write a letter to your friend in Central City, Ohio, put their physical address on the envelope, and place it in a United States Postal Service (USPS) drop box for routing and delivery. A mail carrier retrieves your letter and all the other mail from the drop box and takes it to a local location (post office) for sorting and routing. At the post office, your letter and other items are sorted according to the state listed on the envelope. All mail including your letter that is going to Ohio is loaded onto a truck or plane and transported to a new sorting location in Ohio. At that location, the mail is sorted by cities in Ohio, your letter gets put in the Central City pile and is again shipped off, most likely by truck to a location in Central City. At this location, the mail is all sorted according to the zip code first and then the actual street address, placed with a mail carrier and sent out for delivery. Your friend receives your letter and the process is complete. This is the basic idea of how a network transmits electronic information.
However, we know it isn’t always that simple. Mistakes are made and must be handled for each piece of mail.
This is where the computer network operates on checks and balances in the form of a layered protocol; just like the USPS! We call this layered protocol the TCP/IP Model. There are four layers to the TCP/IP Model; Application, Transport, Internet, and Network Access which is divided between Data Link and Physical layers.
Layer 4 | Application |
|---|---|
Layer 3 | Transport |
Layer 2 | Internet |
Layer 1 | Network Access |
Data Link & Physical |
Figure 1 TCP/IP Model
TCP/IP is the set of protocols on which the Internet operates. It uses the protocols that allow different network elements communicate with each other. Data communication is not possible without TCP/IP model and therefore the Internet would not exist.
Let’s revisit the mail scenario to better understand these layers. The application layer covers the initial scenario from the point of placement in the drop box as described without errors. But what happens when you write the address wrong on the envelope? It gets stamped as undeliverable and returned to you for further action. This is the transport layer in a computer network doing its job. If you did write the address correctly, then the Internet layer takes over moving the letter between large regions or cities without prejudice or concern of what is being sent. Consider the airplane that your letter is on, the pilot does not care what is in the envelope, he only knows it must get to Ohio along with the other thousands of pieces he is transporting. At this point, the next stop is the first half of the fourth layer known as the Data Link layer. Those trucks in the sorting location in Ohio have now assumed responsibility of the mail in relation with their destinations based on city and zip code. The final stop is the physical layer. This is where your friend receives, opens and read your letter. Furthermore, if your friend writes a letter in reply, this too represents the physical layer. Once your friend drops your letter in the mail drop box, we go back to the beginning with the application layer and the process starts all over again.
Now that you have a concrete idea of network operations, we should now look at the scenario from a computer network perspective. In the simplest scenario, you open your web browser, type in a URL, and submit the request. A server somewhere receives the request, searches through its pages, finds the one you requested, and returns it back to you.
Now we expand on this scenario and address the TCP/IP layers. As before, the simple scenario is initiated at the application layer, then at the transport layer, the connection between your computer and the server is established and monitored for errors. If errors are found, you get a return message, most often is the famous 404 error we have all received. If there are no issues, the Internet layer helps move the data from one network to another (from your state to Ohio) where it is then handed off to the Data Link Layer which is typically the Ethernet protocol delivering the information to you (the trucks and the mail carrier transport the letter to your mailbox). Finally, the physical layer is where you receive the requested information on your computer.
Keep in mind that this is the most ideal process description and there are many other issues that can arise. However, for the purpose of this lesson, the scenarios are enough as is.
4.2 Basic Home Networks
Remember that a network can be as few as two devices? This sounds like we can set up a home network easily. While the process is fairly simple, it must be done precisely, or it won’t work. If you follow the basic steps below, you can be well on your way to your own home network. As with anything in the computing world, there are many other options besides these basic steps. For the purpose of this course, only the bare basics are covered.
Getting Internet Access
It is wise to think about what you will be doing with your network devices and how many devices you will connect. The number of devices and your Internet activity will be a strong factor in the Internet transmission speeds you will need. You can call your local Internet Service Provider (ISP) and their techs can walk you through the best Internet package you should subscribe to, based on your answers to those questions. The ISP will set up an appointment to install your Internet access. Typically, most ISPs will provide the modem with wireless access for a monthly fee. If they only provide a modem, no worries, you can buy your own wireless router.
Wired Setup
If you wish to have a computer directly connected to the Internet via a wire, you can do so with an ethernet cable. You will plug it directly into your modem or router and connect the other end to your computer. This will give you the most optimal speeds from your ISP.
Wireless Setup
Once you have your Internet installed and you can set up your wireless by following either the instructions given by the ISP or the instructions provided with the wireless router. Be sure to secure your access point with an appropriate password. This will prevent anyone outside your home from accessing your Internet.
Add Wireless Devices
Using the access password that you created, you can now go into the settings of your wireless capable devices and connect each to the wireless signal. You can typically connect laptops, tablets, mobile phones, printers, gaming consoles, smart TVs and much more. Keep in mind that the more devices you have actively accessing the wireless signal at the same time, the slower your speed will be.
And there you have it! The basics of a home network setup. You can view a diagram below to see what a basic home network looks like.
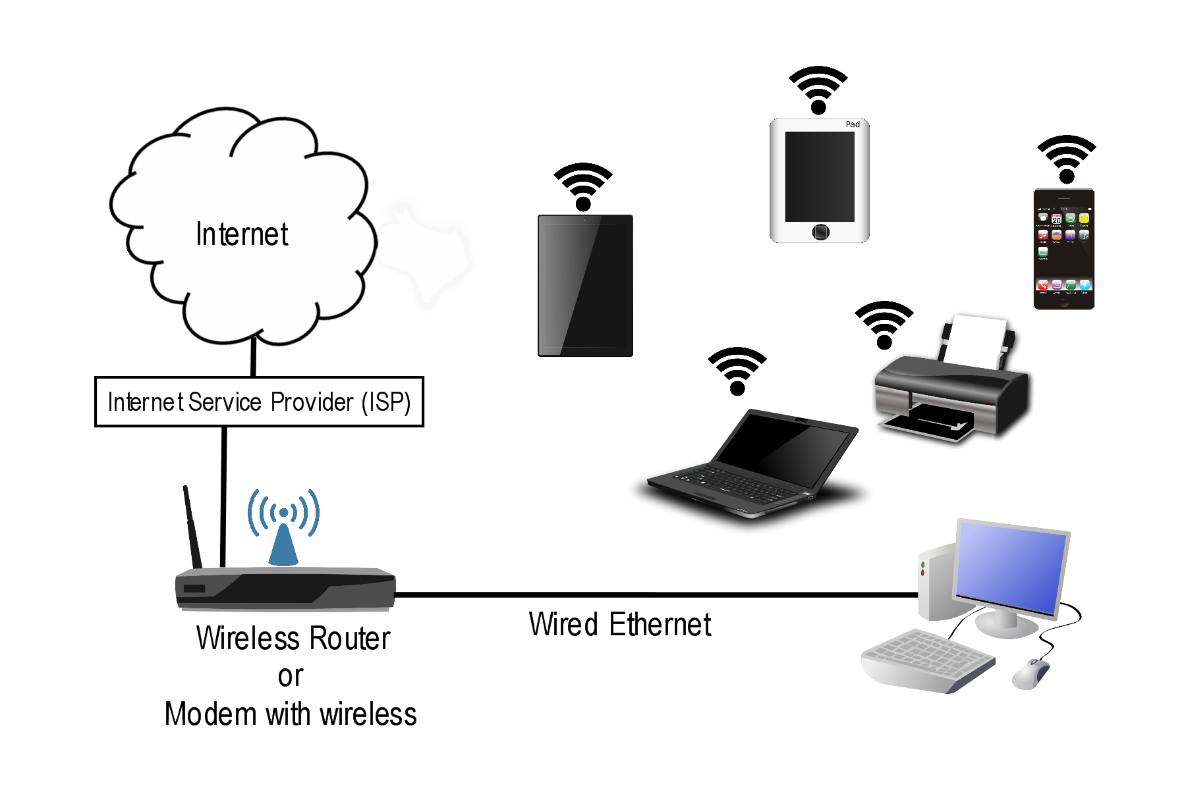
Module 5
Suggested Learning Activities
Discussion
Question: Think of a task where sequence of instruction matters. Is there a way to modify it to where sequence doesn't matter? Write it out for your classmates to review and give feedback.
Discuss your answer in detail. Engage at least two classmates with feedback on their solution. Do your best to defend your position with more facts than opinions!
Minimum requirements:
- Respond thoughtfully and respectfully to at least two classmates.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Cite any and all sources.
Homework
Think of three day-to-day tasks that you do regularly. You will write describe each of your chosen tasks and identify what parts could be written out as a conditional or looping structure as it relates to programming. The you will write them out in pseudocode statements with the proper structure and indentations. There is an example/hint at the bottom of this assignment to help you on the pseudocode portion.
Minimum requirements:
- A minimum of two full paragraphs describing each task and their related conditional and/or looping structures (6 paragraphs total)
- One full pseudocode statement for EACH task with proper indentations, syntax, and structure (three pseudocode statements total)
- Submit only one document.
- Use paragraph structure where necessary. Use complete sentences where necessary and proper grammar and spelling.
- Place a header on your page that contains your first and last name, the assignment name, and the course code identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
HINT:
This is a generic Algorithm:
- Put a teabag in a cup
- Boil some water
- Add water to cup
- Remove the tea bag
- Add sugar
- Add milk
- Stir
- Serve
Below are some possible pseudocode statements for step 5 ONLY, you will need to write out the appropriate syntax and structure for ALL steps to include any implied steps in between.
IF (want sugar)
THEN (add sugar);
ELSE (don’t add sugar);
ENDIF
WHILE (want sugar)
Add teaspoon of sugar;
ENDWHILE
Project
Think of three simple tasks where you believe sequence of instruction matters. Is there a way to modify it to where sequence doesn't matter? Find steps in each task where the sequence can be changed and still achieve the desired outcome. Write out the original and modified algorithms AND pseudocode for each task. Write a short paragraph for each task describing the changes in sequence.
Minimum requirements:
- A minimum of one paragraph for each of the three tasks (three paragraphs total).
- Two algorithms and two pseudocode statements for each of the three tasks (6 algorithms and 6 pseudocode statements total)
- Submit only one document.
- Use paragraph structure. Use complete sentences and proper grammar and spelling.
- Include a cover page that contains your name, the assignment name, and the course code identifier.
- Your document must be one of the following formats (.doc, .docx, or .rtf).
- Cite any and all sources.
Assessment
The goal of this project is to test your knowledge of the basics of programming structures. More specifically, you will design your own algorithm using both pseudocode and a flowchart.
Think of some daily activities that you perform. You are going to prepare a plan and design an algorithm that can be translated into a program that would tell a computer how to do the activity you have chosen.
- In paragraph form, describe in detail the big picture, the final goal, and the individual stages of your algorithm. If there are issues to overcome, write out possible solutions for each. Also, describe your inputs, outputs, decisions, and repetitions in the algorithm. Think about sequence when writing this out.
- Using the standard notation for pseudocode that you have learned, write out the algorithm for the daily activity you have selected. Be sure to indent where required.
- Using your pseudocode from step two, create a flowchart of your algorithm. Utilize the correct symbols in your flowchart that you learned about in the module.
- Submit your work.
NOTE: Remember that this is an assessment, put some thought into this and be very thorough and extensive in your submission. Minimalistic work is not sufficient will be graded accordingly.
FINAL ASSESSMENT
This is the final project!
The goal of this project to showcase what you have learned. You will create a PowerPoint Show that will serve like a portfolio of your journey in the course. In your presentation show you will embed documents from your independent projects, identify your favorite topic(s) and least favorite topic(s) in the course, explain why you liked or didn't like them, identify at least three new things that you have learned in the course and will continue to use.
Minimum requirements
- A minimum of eight slides not including the title slide and the resources/references slide.
- One slide for each of the five modules. You will embed each of your Independent Project documents in the appropriate module slide and describe what you learned in that module and project in short bulleted lists.
- The remaining three slides can cover liked topics and why, disliked topics and why, and three new things learned in the course that you will continue to use.
- You must apply or include slide transitions, images, themes, and animations on all slides.
- It must be clean, informative, and aesthetically pleasing. Check for spelling and grammar!
- You will need to save your presentation as a PowerPoint Show (.ppsx)
Submit your completed PowerPoint Show via the project submission link.
NOTE: Remember that this is an assessment, put some thought into this and be very thorough and extensive in your submission. Minimalistic work is not sufficient and will be graded accordingly.
5.1 What is computer programming
Recall back to Module 1 where we discussed hardware and software. We learned that software is what tells hardware what to do by providing instructions. The instructions solve a problem of some sort. Now you may say that needing to send a print job to the printer is not a problem but it actually is. Anything that we desire to do requires a set of instructions or steps to follow to get to the end result. This makes everything we do a problem with a set of instructions to gain an end result. A program is that set of instructions created to solve a problem (complete a desired task) and therefore programming is the creation of those instructions. With respect to computers, the set of instructions are for the computer to carry out and accomplish an end result. In order to do this, there are some basic concepts/structures to use
There are three common concepts and structures for computer programming. First, you have to have a sequence of instruction. This means you have the right instructions in the correct order. This is very important in any set of instructions for a computer. Think about the sequence of getting dressed. Do you put your undergarments on first and then your outer garments? Of course, you do! If the sequence was followed out of order, say, you put your coat on and then your pants and decide that now you need to put on your shirt and undergarments, you are in a bit of a debacle. Following the correct sequence is essential to success in reaching the desired end result! On occasion, there are instructions where the sequence isn’t as important. Where this occurs, we lean on a more predictable order or standard based on norms relative to culture. Think about the writing of an address on a piece of mail in the United States. We learn in school to address an item in a certain sequence. However, the postal service workers use the exact reverse of this order to get the item delivered.
Next, we talk about conditional structures. This is where decisions dictate the next step followed, such as considering if something is true or false and then performing an action based on the answer. These decisions help determine separate outcomes based on the decision made. This is why they are called conditional structures. The condition determines the route of the instructions. These are typically called if statements in computer programming and follow the order of IF…THEN…ELSE. If we do this, then this happened, otherwise if we don’t then this happens.
Finally, there are looping structures. These differ from the conditional because there are not multiple different outcomes; the statement requires a repeat of the same instructions until a condition occurs or repeat of the same instructions to maintain an existing condition. Most often these statements in computer programming are simply to do something a specified number of times and stop or an unspecified number of times until a condition is met and then stop.
5.2 Programming Strategies/Algorithm Design
Computer programs can range in size and complexity. For simple tasks like turning on a light, there are very few instructions and really no need for a strategy. However, for more in-depth tasks you shouldn’t think of starting to code without using a strategy to work through the logic of the program. We consider what the problem is and design an algorithm to work through and solve the problem. An algorithm is the plan we write out to solve our problem.
When we solve any problem we most likely try to look at different pathways to get to an end result. Then we try to process which of those pathways is the best route to take. Sometimes there may be more than one way that seems the best route. Designing an algorithm will help us narrow down our choices and determine if there really is a best solution.
To create an algorithm we must know what our desired end result will be and we must consider all of the potential issues that we will meet while working towards that end result. The basic things to consider and ensure you understand the problem is to decide what the inputs and outputs will be, are there any decisions to be made or any steps that will need to be repeated, and what order will these steps need to be in. Once you have all of this, then you are ready to write out the algorithm. We will discuss two common algorithm design methods that work very well and have been used for many years; flowcharting and pseudocode.
Flowcharting is a method of mapping out the program based on the major concepts or structures it will need. This will help to visualize the logical flow of the program. A flow chart is a diagram of standard symbols that represent the step-by-step instructions to solve the problem. The most common flowchart symbols are shown below.
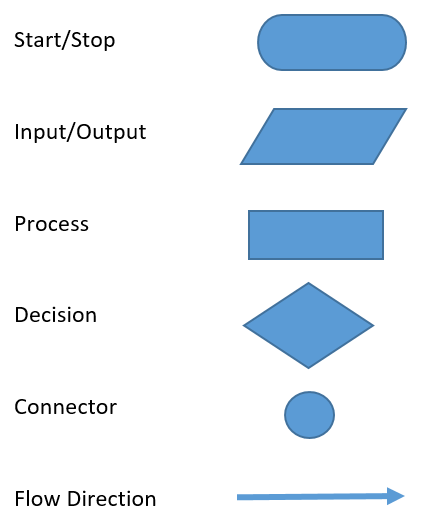
Pseudocode is basically the algorithm written out in standard wording somewhat like an outline. There are not defined standards for writing this out however certain notations and structures should be used anyway. The most common notations are:
- Input
- Output
- While
- For
- Repeat-Until
- If-Then-Else
Also, typically when writing steps that reside inside the last four items, you should indent the text.
These design methods seem time-consuming and almost unnecessary, right? This is because our brains usually work autonomously without all of this explicit guidance. A computer, on the other hand, needs these well thought out and very specific instructions. There is a saying in the computing world that a computer is only as smart as the person using it. It may be safe to say that a computer program is only as smart as the person who wrote the code! Computers are not sentient beings, they need us, humans, to tell them exactly what to do!
Complete the tutorials found at the link below for more information.
https://www.bbc.com/bitesize/guides/z3bq7ty/revision/1
These tutorials are provided by the British Broadcasting Corporation’s Bitesize resource and cover the following topics.
Designing an Algorithm
Pseudocode
Flowcharts
Work through the Designing an Algorithm module. Be sure to click on the hyperlinks if you need more information! Review all three pages and then take the test. The test is not graded but will provide you a good feedback on your understanding of the content.